Access Mapping
Access Mapping is a crucial workflow in TRASAGATE that allows administrators to explicitly assign users or user groups to service profiles, defining who can access which resources and how. This process is essential for enforcing granular access control policies and maintaining the principle of least privilege.
Prerequisites
Before you can map access in TRASAGATE, you need to have the following components defined:
- User Profiles: The users or user groups you want to grant access to.
- Service Profiles: The services or applications you want to control access to.
- Access Policies: The rules that govern how users can access the services, including factors such as device posture, location, time, and authentication requirements.
Access Mapping Methods
TRASAGATE supports three main methods for mapping access:
User-to-Service Mapping: This method allows you to map a single user directly to a specific service. This is useful for granting access to individual users who require unique permissions or have specific roles within your organization.
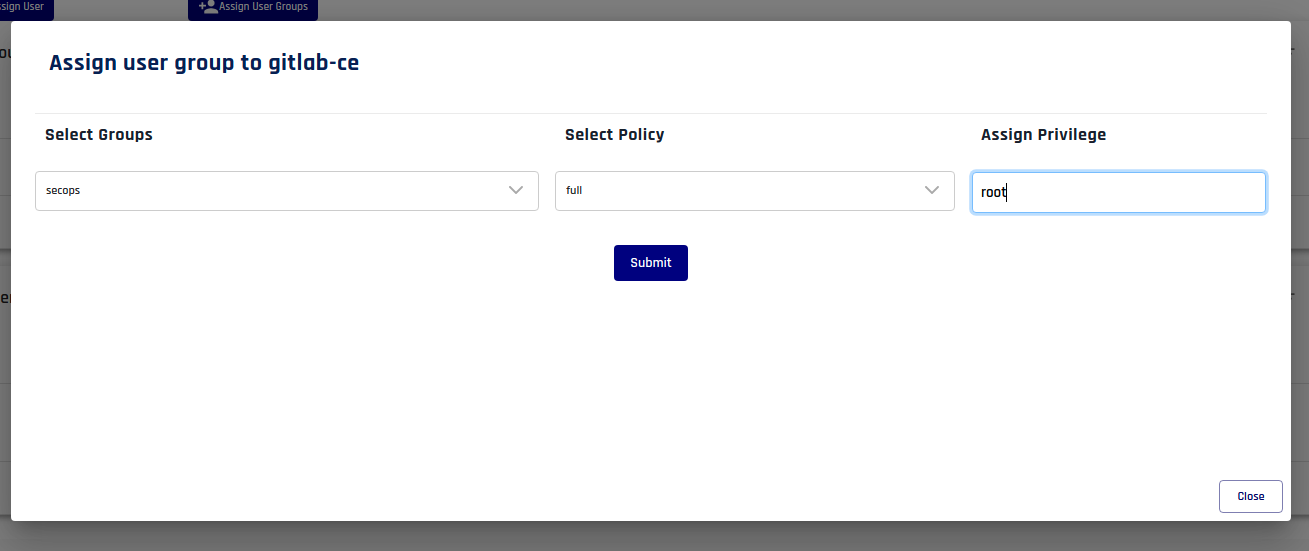
User Group-to-Service Mapping: With this method, you can map an entire user group to a service. This is an efficient way to grant access to multiple users who share similar roles or responsibilities, as it allows you to manage access at a group level rather than individually.
User Group-to-Service Group Mapping: This method enables you to map a user group to a group of services. Service groups are useful when you have multiple related services or applications that share similar access requirements. By mapping a user group to a service group, you can grant access to all the services within the group at once, simplifying access management.
Benefits of Access Mapping
By using TRASAGATE's access mapping functionality, you can:
Enforce Granular Access Control: Map access based on user roles, responsibilities, and business requirements, ensuring that users only have access to the resources they need to perform their jobs.
Simplify Access Management: Manage access at a group level, reducing the administrative overhead of individually assigning permissions to each user and service.
Maintain the Principle of Least Privilege: Continuously review and update access mappings to ensure that users maintain only the minimum level of access required, reducing the risk of unauthorized access and data breaches.
Streamline Onboarding and Offboarding: Quickly grant or revoke access to multiple services when users join or leave your organization, or when their roles and responsibilities change.
By leveraging TRASAGATE's access mapping capabilities, you can establish a strong foundation for zero trust access control, ensuring that the right users have access to the right resources at the right time, all while maintaining a high level of security and compliance.