Zero Trust Access with TRASAGATE
Secure Access to Diverse Environments
Zero Trust Architecture
Granular Access Control
Seamless User Experience
Continuous Monitoring and Auditing
Scalability and Flexibility
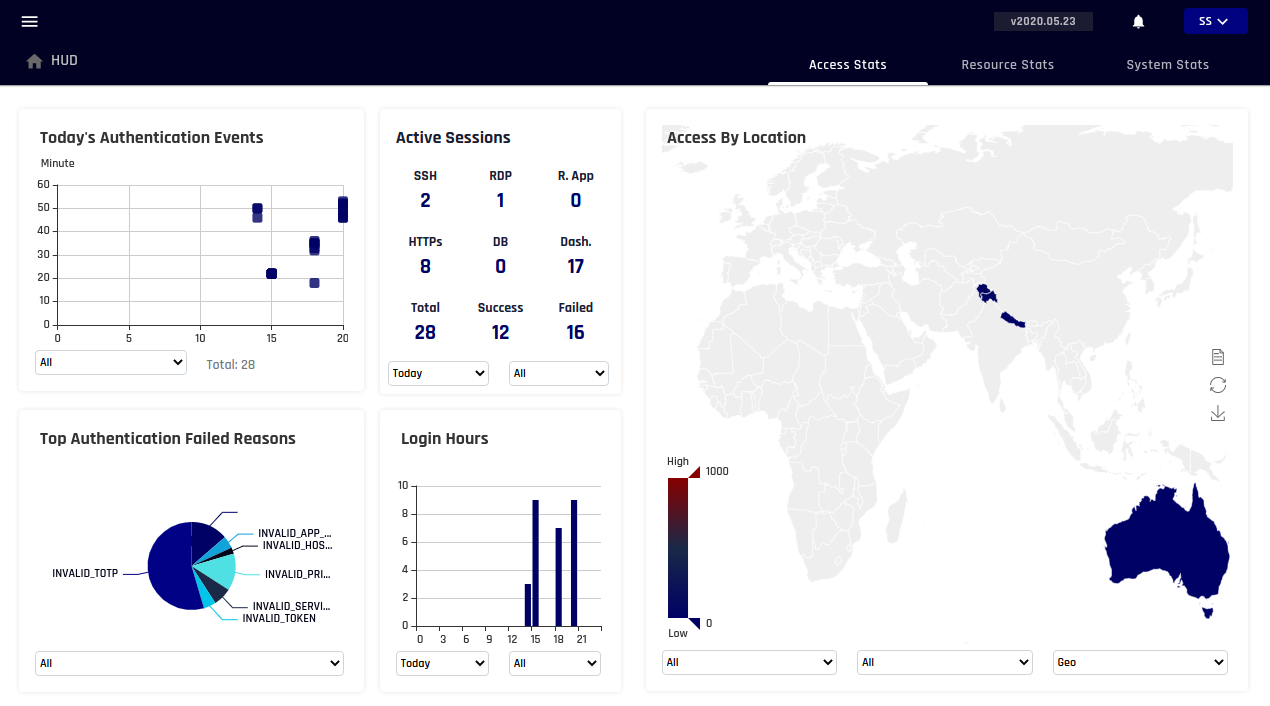
Why You Need TRASAGATE
In today's rapidly evolving IT environment, organizations face the challenge of managing secure access to a diverse range of systems—data centers, cloud infrastructure, ephemeral services, and dedicated servers. As businesses embrace hybrid models, integrating managed service providers and internal teams, security becomes more complex. The traditional perimeter-based security model is no longer sufficient.TRASAGATE is a cutting-edge solution designed to meet the demands of modern IT environments by implementing a robust zero trust access model. Zero trust operates under the premise that no one inside or outside your network is inherently trusted. Every access attempt, whether from an internal user or an external provider, is meticulously verified through multi-factor authentication, real-time monitoring, and encrypted connections.
This makes TRASAGATE ideal for businesses of all sizes looking to manage remote access across various platforms and services. Whether you’re securing sensitive data on a dedicated server or granting temporary access to cloud resources, TRASAGATE provides the assurance that only authenticated, authorized, and compliant users and devices will have access.
Why TRASAGATE?
TRASAGATE offers a comprehensive and secure approach to managing access to your organization’s critical infrastructure. Built on the Zero Trust principle, our platform guarantees that all users, whether internal or external, are continuously authenticated, authorized, and their actions are monitored across every session.
Our platform supports businesses in securing remote access to essential services such as Web, SSH, RDP, and databases, making it easier than ever to ensure that sensitive information remains safe, even in distributed and remote environments.
Secure Remote Access
TRASAGATE ensures secure remote access by implementing an identity-aware access proxy, privileged access management, two-factor authentication, and device trust policies. These features ensure that only trusted users and devices are granted access to Web, SSH, RDP, and database services, safeguarding your infrastructure at every session.
Geo spanned access point.
Distributed teams and distributed edge computing is the new norm for modern tech-driven teams. TRASAGATE can be deployed as Geo spanned access points, protecting internal infrastructure access with the highest availability. Configure from a single dashboard, and policy will be synced automatically to every access point.
Integration with Identity and Secret Providers
Unlike legacy access control systems, TRASAGATE directly integrates with an existing user identity provider, service identity providers, and secret managers to protect dynamic infrastructure. TRASAGATE adapts to existing workflows.
Unified Access Control Platform
A unified security platform that can address every access control security requirements for your team. TRASAGATE enbles best practice security by default.
Privileged Account Management
Single Sign On for HTTPs, RDP, SSH
Policy Defined Access Control
Password and Keys Vault
Session Audit
Two Factor Authentication
Trusted by Leading Enterprises
We are proud to partner with organizations across various industries, providing them with a robust platform that ensures their infrastructure is secure and their data is protected. Our customers trust TRASAGATE to provide secure access management solutions for a diverse range of use cases, from remote workforce management to securing cloud-based applications.